Re-Thinking Social Media part 6 - Identity Controls
Note: this article was originally posted in 2018.
In our series on Social Media thus far we've covered a wide variety of topics including the fundamental flaws with both the business models and platform architectures of Low-Trust Social Media as well as some of the ways that these flaws have been exploited and the implications to both the tech industry and society in general. In today's article, I'm going to spend some time reviewing what the appropriate controls ought to be for managing Identity on a High-Trust or responsible Social Media platform. These Identity controls are arguably more important than the Content Controls (which we covered in article 4) for the following reasons:
Without the proper Identity controls, the Social Media companies - regardless of the amount of money or manpower they may throw at the content problem (or other related ones), will never be able to keep pace with the threats and / or abuse occurring on their platforms. This is because any platform that allows bad actors into their environment in the first place is fundamentally compromised. This is not a new concept - all of information security is predicated on stopping this from happening.
Identity is also the key safeguard for securing all / any commercial activity. For Social Media to evolve and succeed in the future, it must move to business models based upon commerce. Continued attempts to try to monetize or exploit user data as opposed to developing real revenue-generating services are doomed to self-destruct. This self-destruction may already be happening as we speak.
Continuous monitoring and management of user behavior - tied to Identity - is the primary factor that will provide both trust in the platform as well as a positive experience for all of those using the platform. This does not imply authoritarian measures like those being employed right now in China - rather it refers to preventing the relatively small percentage of bad actors from more or less ruining the user experiences of everyone else. Those bad actors aren't tracked for political subversion (as in China) - they're just Blacklisted and kicked out for behavior that they agreed not to engage in (upon enrollment). This is a tried and true technique - it works in all other contexts related to IT as well as society and it will certainly work for Social media.
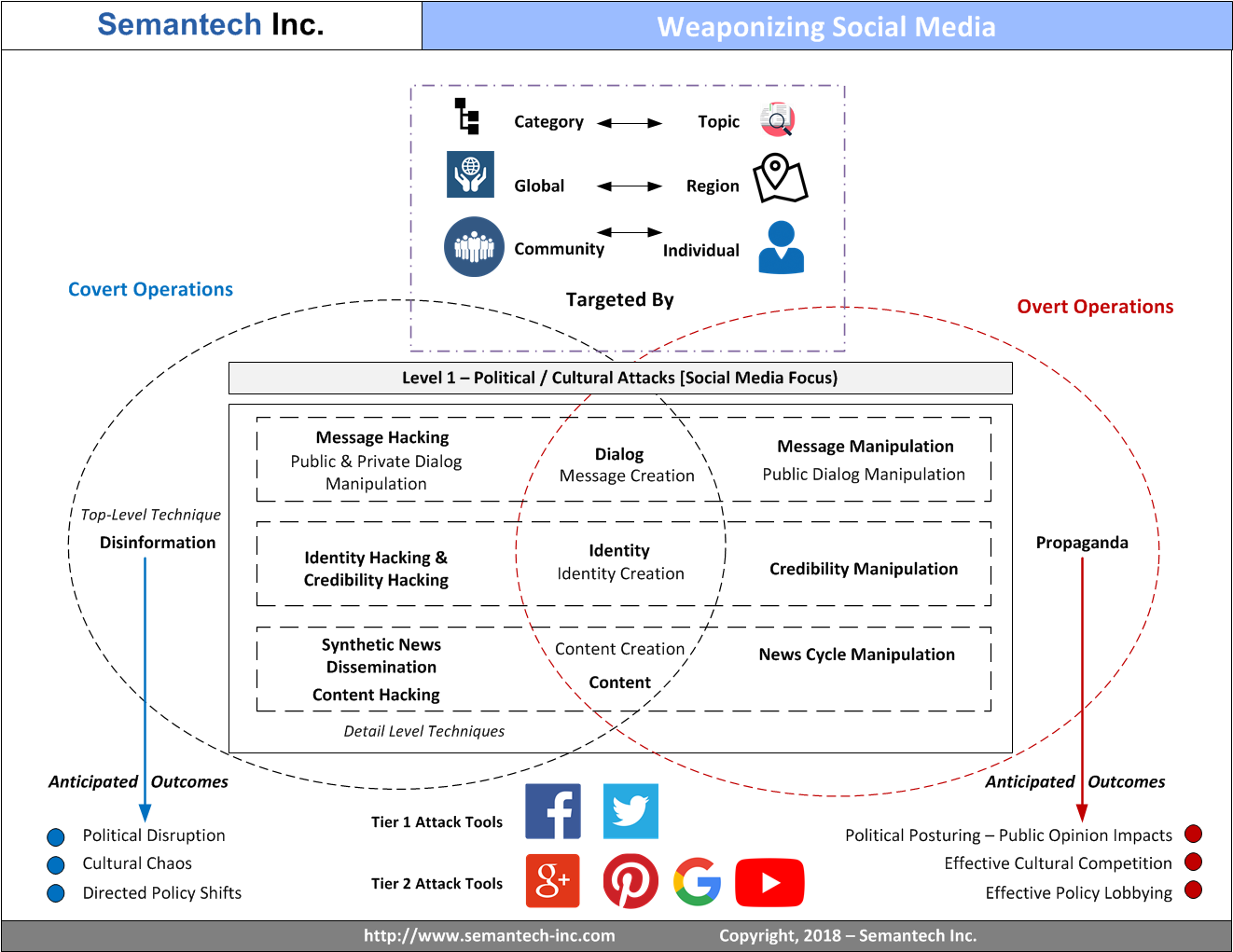
The diagram above places Identity in the center of all platform security (w/ a particular focus here on political attacks)...
Perhaps the best way to discuss Identity Controls is in the context of an "Identity Lifecycle."
Identity Lifecycle, defined: The Identity Lifecycle is the cradle to grave management approach for any given Identity within a specific or shared platform context. All Identity controls must fit within this context and the expectation is that the Lifecycle is dynamic in nature (in other words, it must continuously evolve to match the threat landscape). The main premise for this Lifecycle is assuring that the identity is a real person and not a bot or a bad actor posing as someone they're not.
The Identity Lifecycle stages include...
Initiate: Assurance of real identity
Monitor: Ongoing determination if behavior is consistent with that real identity
Interact: see below
Retire: Properly close out the lifecycle to eliminate any potential vulnerabilities
Behavioral Level Interaction
Reward - Enhance opportunities for positive behavior on the platform/s
Punish - Remove opportunities for negative behavior on the platform/s
System Level Interaction
Integration - of other control families within the platform as well as with external partner platforms
Facilitation - of processes & services (both within and across platforms)
If we were to overlay the Identity Lifecycle onto Social Media Platforms, it might look something like this:
Initiate Controls:
Enrollment 1 - Identity Interrogation (first step - using two-factor authentication)
Enrollment 2 - Identity Validation (secondary identity mapping against both fake and real existing identities - could use AI and may include Biometrics or other records - must support future e-commerce level security).
Enrollment 3 - Behavior / Use Agreements (most become more explicit both in expectations and possible penalties for abuse - the candidate will have to read it - designed in such a way to be bot-proof)
Probationary Period - The 1st three months would apply a stricter level of behavioral monitoring and potentially reduced set of privileges
Assign initial privilege set/s
Assign initial credibility rating
Preliminary and ongoing credibility ratings could be based on the following (or similar) paradigm:
Level 1 - Highly credible, preferred access
Level 2 - Credible, full access
Level 3 - Low Credibility, limited access
Level 4 - Not Credible, access denied
Monitor Controls:
Continuous commerce & marketing scam monitoring
User-driven Behavior Reporting
Content "Identity" lineage assessment (for re-posting of unknown sources)
Continuous bot behavior assessment
Continuous user credibility assessment
Continuous cross-platform identity awareness (collaborating to review behavior issues on shared identities coming from external / partner platforms)
Continuous Identity & Privacy protection
Interact Controls:
User credibility rating updates
User-driven privacy services
Coordinated user rewards
Coordinated user penalties
Levying of Suspensions, or account Restrictions based upon behavioral infractions
Updating of user privileges based upon the above actions
Coordinated industry-level identity Blacklisting (for users, groups, content sources)
The final stage, Retire, is associated with controls that ensure the Identity and related privileges are properly removed and stored for future reference and identity mapping purposes.
In our next article in this series, we'll explore how the Social Media Content & Identity controls might function in some typical real-world scenarios and then in our final article in this series, we'll discuss the future of Social media in the context of Next-Generation monetization opportunities.
Copyright 2018, Stephen Lahanas