A Framework for Hybrid Cyber Warfare
Note: this article was originally published in 2018.
This article is the first in a three-part series which will explore in some detail how specific technologies have been exploited in unanticipated ways over the past several years and how those exploits have helped to define a new wave of "Hybrid Cyber Warfare." The goal of the first article is to present and define a Framework for Hybrid Cyber Warfare. The second article will be titled - Democracy Hacking, how Social Media is Weaponized and represents a deeper dive into one of several current weak links in the Framework. The third article will address specific suggestions in relation to how emerging technologies can be protected to avoid becoming Weaponized within the larger Hybrid Cyber Warfare Framework.
So, why is it useful to represent or otherwise define something like a Hybrid Cyber Warfare Framework? The obvious reason is that for all of the talk about Cyber Security and its impact on every aspect of society, there still isn't a good way to quantify what is and what isn't Cyber Warfare (as opposed to Cyber crime etc.). I took my first stab at defining that about year in this article - the focus in that article was on the key principles that would help to define Cyber Warfare. It was a good start, but failed perhaps to provide a more quantifiable set of characteristics which could be used to classify various forms or types of Cyber Warfare. And returning to the question as to why this all is so important - essentially, the reason why is that if we don't have a comprehensive, agreed upon foundation it becomes exponentially more difficult to determine appropriate responses or defensive measures.
All military action, whether overt or covert in nature must flow from Doctrine. Doctrine drives strategy and strategy drives tactics and this applies both from offensive and defensive perspectives. For better or worse, the modern battlespace now includes a Cyber domain, but unlike some of the other military domains, the Cyber domain cuts across every other domain. In other words, every military capability is now wholly dependent on various Cyber capabilities, thus any potential military conflict is already partially Cyber Warfare. Some conflicts are also purely Cyber in nature, however, as we know well, Cyber attacks that are non-military in nature are certainly no longer exclusively focused on virtual or IT related capabilities. Every other industry is as dependent on Cyber capability as military organizations and so non-military Cyber attacks can certainly be qualified as warfare if the intent of those attacks is to weaken, disrupt or destroy an adversary's ability to operate normally. Building a more robust Cyber Warfare doctrine, begins by understanding the relationship between Cyber and non-Cyber capabilities, between direct and indirect military operations and between the myriad of "Hybrid" combinations that are now possible given recent technological advances. This Hybrid Cyber Warfare Framework is meant to stimulate a discussion in regards to definition of a new generation of Cyber related military doctrine.
However that begs an important question; what exactly is wrong with or missing within current military doctrine? Well, here are several suggestions as to why current doctrine may be falling somewhat short:
While current Doctrine acknowledges a relationship w/ non-military capability (often referred to as Defense Industrial Base or DIB), the definitions as to who or what belongs to the DIB may be somewhat limited as opposed to what it ought to encompass.
Current Doctrine and standards associated with security controls (NIST, FISMA etc.) have done a great job of defining defensive capability in regards to traditional network defense; however this does not take into account other types of attack or properly recognize emerging technologies (such the Internet of Things [IoT], Social Media and Artificial Intelligence, etc.).
Current doctrine tends to view threats from a two-dimensional perspective. In other words, it doesn't fully recognize or accommodate complex Hybrid scenarios. In some respects, it is like treating the symptoms without understanding the disease - thus making root cause solutioning impossible except through accident.
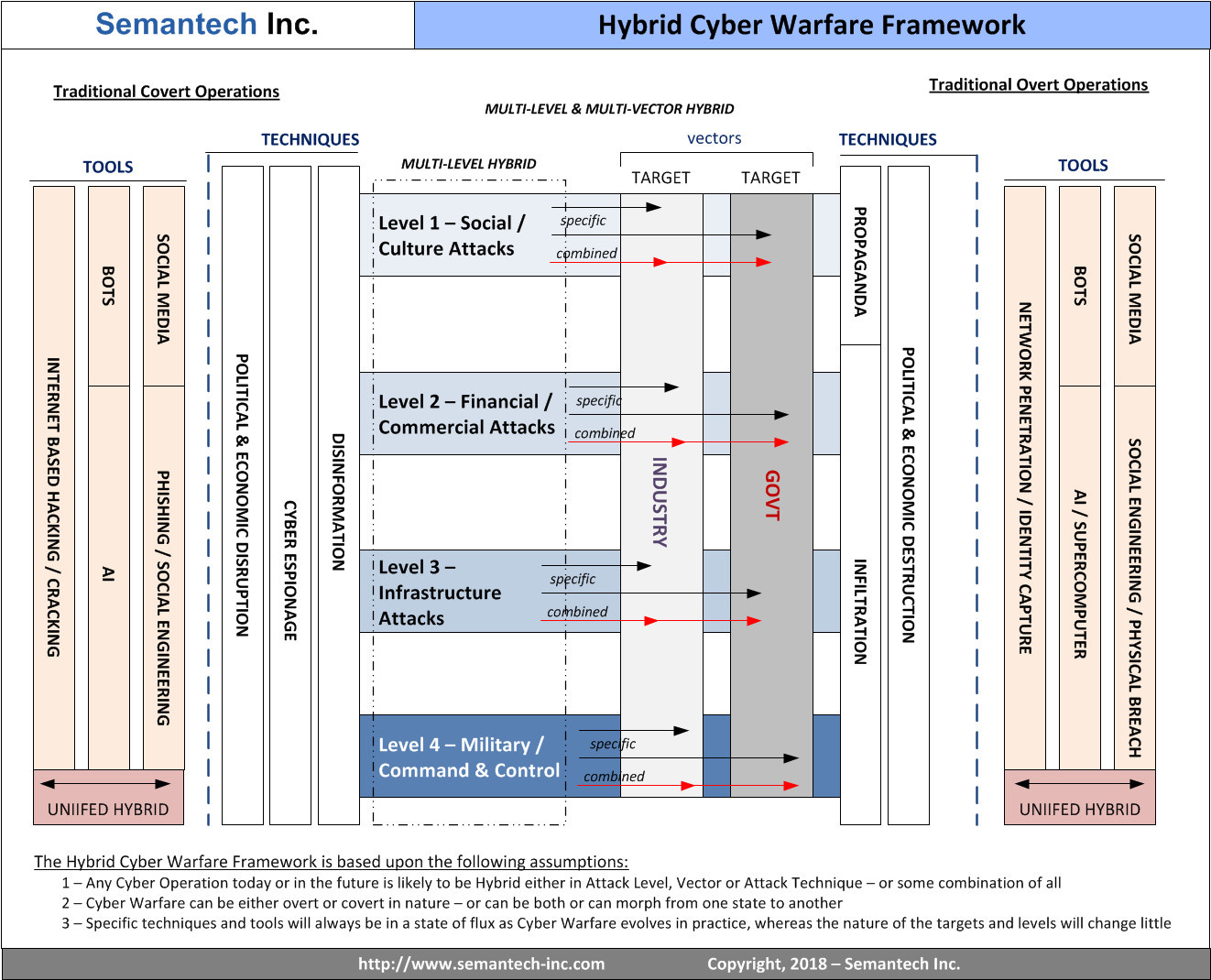
Let's take a look now at what a notional Hybrid Cyber Warfare Framework might look like:
The key elements of this view include the following:
1 - The Framework must acknowledge the boundaries between traditional covert and overt military operations. The illustration above highlights where those boundaries are logically, however in reality those operations today extend into the Cyber Warfare Framework (the middle) in every possible scenario (or you could that Cyber extends into them in both direction).
2 - The Framework must be able to track techniques and tools in context with the types of attacks and types of targets as well as the types of outcomes anticipated. One of the major differences between this proposed Framework and current practice is the ability to focus more on the target and outcome matrix as opposed to the mere attack configuration. In other words, in current Information Assurance (IA) paradigms, we view something like DDoS (Denial of Service Attacks) as a primary focus due to the perimeter controls focus most organizations follow. However, in today's reality, DDoS is almost always part of a larger context - in other words a Hybrid attack. The focus should be on the attack and its anticipated outcomes as opposed to just the mechanism of the attack per se. Obviously, the immediate attack must be stopped or countered, however we'd be missing the point if we didn't understand what the adversary was trying to accomplish. A traditional military analogy might be a focus on providing suppressing fire against a company of soldiers immediately ahead while ignoring the battalions or divisions flanking you.
3 - The Framework is divided into portions which are relatively stable and those which or more or less permanently dynamic. The attack levels and vectors may be better defined at some point, but will remain relatively stable. The techniques will be somewhat more flexible, with new ones coming into being as emerging technologies make them possible. Others which be more traditional will change in nature but remain focused on many of the same goals or outcomes. The part of the Framework which will be permanently dynamic will be the Tools portion. Acknowledging this part is critical as missing any change here risks securing against yesterday's threats at the expense of today's and tomorrow's.
4 - Ultimately the goal for any such Framework is that it must be comprehensive and flexible enough to extend in any direction needed to develop more detailed Doctrine, Strategy or Tactics. It must support deep dives while simultaneously acknowledging the ability to link aspects of the Framework together in an Agile fashion to represent Hybrid scenarios.
The view above presents several areas in the Tools section that probably stand out - either because it is obvious we haven't properly addressed them yet (as in Artificial Intelligence) or may seem odd that they'd be listed here at all (as in Social Media). About a year ago, I wrote a series of articles on the controversies surrounding the 2016 election (which in no way have diminished since then). In those articles, I spent some time highlighting how Social Media was manipulated by foreign governments to further their ends. In the next article in this series, I will take a deeper dive into Social Media vulnerabilities and relate those to the Hybrid Cyber Security Framework presented here.
Copyright 2018, Stephen Lahanas